
Guardians of Data: How Role-Based Access Control Reinvents Security
In the ever-changing digital landscape of the present day, data security is no longer … Read more

What are the main five types of Cybersecurity?
Cybersecurity is the practice of safeguarding organizations and individuals against cyber threats and unauthorized … Read more

Does Windows 11 need an antivirus along with Windows Security?
It has been almost two years now that Microsoft’s latest version of Windows, that … Read more

What is DNS over HTTPS – Secure DNS and how does it work?
DNS over HTTPS (DoH) is a free protocol standard for transmitting DNS requests (and … Read more

3 Ways CIOs/CISOs can Tackle Cybersecurity Challenges from Emerging Technologies
By Mr. Amit Luthra, Managing Director – India, Lenovo ISG In this evolving digital … Read more

Top challenges Security Operations Center (SOC) teams face every day
Apart from the unknown challenges of identifying attacks, SOC teams constantly face issues that … Read more

What is Incognito? How to access it in different browsers
Incognito mode is a tool to protect your online privacy. In a browser, it … Read more

VPN – Virtual Private Network: Usage and types
We are living in a parallel virtual world today where a major portion of … Read more

How to increase your Internet security to surf safely and privately
Internet is one of the greatest things that surely revolutionized the whole world and … Read more
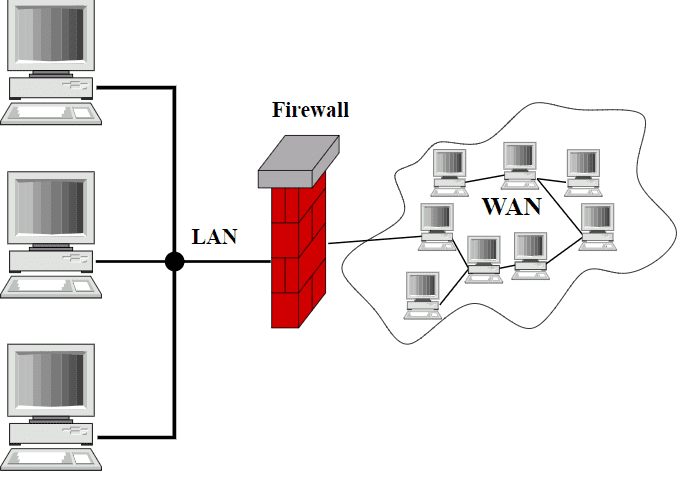
Firewall technology and what are the 3 basic types of firewalls
A firewall- as the name indicates- is a Fire like Wall that protects your … Read more

PORT 445: What is the use and how to disable this TCP port
The WannaCry ransomware halted thousands of computers around the world in the spring of … Read more

Everything You Need to Know About Pegasus Spyware
We’re sure you’ve seen a flurry of news reports and lengthy social media posts … Read more

How to disable print spooler service Windows 10
Here are the steps to disable the Windows 10 Print Spooler service to save … Read more


