We are living in a parallel virtual world today where a major portion of the urban population is dependent on the World Wide Web as a source of information. It is almost impossible to imagine a life without the internet as it has become an integral part of our daily routine. From using multiple online services to fulfill our day-to-day requirements to accessing networks for our daily dose of entertainment, the internet has done it all. There are two types of networks that we generally utilize.
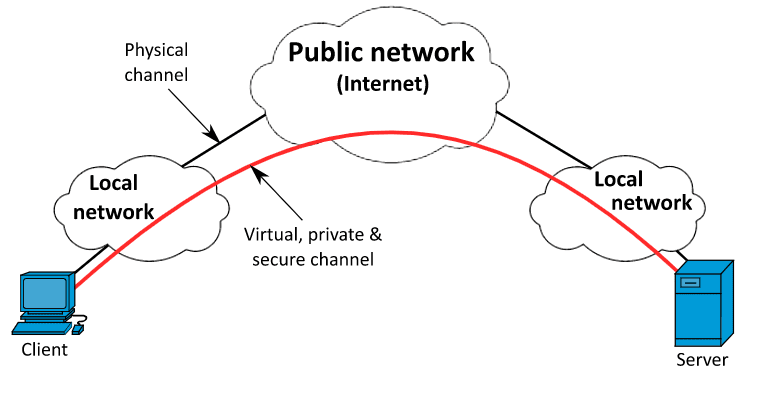
To access the network, one must have a modem or router installed at his end. When you use these connecting devices to transfer data to your smartphone, smart TV, and other smart devices at your home, it’s called an Internal network but when you use this network to access data and services outside your personal space i.e. the outer world, it’s simply referred to as an External network. Whether you are watching a video on YouTube or simply type ‘google.com’ in the search tab to access the Google homepage, the process of acquiring the required information is quite similar.
When you try to access the Google homepage via your modem or router, a request is sent to the corresponding server or data center with your virtual address and the server in which the required page is stored responds to your IP address with the desired content. Now when you start exploring the digital world, security concerns will always play their part in worrying you about your online safety.
Several risks are associated with the usage of an external network-
- Your Internet Service Provider (ISP) has the capability of tracking your online activities. It can track the websites you are going to. It knows your IP address and the IP addresses that you are more often sending requests to. Government and certain external sources can also intrude on your online space.
- One might feel overjoyed while getting access to a free Wi-Fi network but it’s as risky as using a sharp knife without any precaution. The data that you transfer or receive using an open network is not at all safe and can be stolen by the expert hawkeyed hackers out there as the transmission may not be encrypted every time.
- If you are not using a secured network, your privacy is definitely at risk.
All of the above-mentioned shortcomings and threats can be reduced by using VPN which stands for Virtual Private Network.
Why is VPN needed?
Virtual Private Network was first developed in 1996 by Microsoft to enable remote employees to access the secured connection of the company from anywhere. This actually doubled the productivity of the organization, encouraging other companies to explore this new technology as well.
- To resolve the major concern of privacy-related threats, one should always use VPN, most importantly while streaming videos, using public Wi-Fi while traveling, playing games, and browsing online shopping sites as the conversation between you and the VPN server is completely encrypted so that neither your ISP nor any other external malware can peep into your online space.
- You can also access the content of blocked or restricted websites that are bound to a particular region or country by using a secure VPN. For example, if you are traveling to China and unable to access Facebook as it’s blocked there, you can access it by logging in to your VPN server. There are many free and paid VPN services available but it’s recommended to use the paid services as the free VPN might not be as secure and reliable to use. You can also find inbuilt VPN services in your smartphone settings.
Usage of VPN:
The moment you start sharing your personal information over the internet while making online payments or transactions, you open a window for unwanted threats to invade your privacy. Let us dig deep into how useful and crucial VPN can be to protect your virtual world experience-
- VPN provides you with a protected network connection while using public networks. It encrypts your internet traffic and hides your online identity which makes it difficult for third parties to look into your personal data and reduces the risk of data theft.
- VPN connects your PC/ smartphone to a server computer which enables you to browse the internet by using the secured connection of that computer.
- VPNs are entirely legal and reliable, this is why VPNs are being used by a lot of individuals as well as organizations to safeguard their data from hackers. VPNs are also used in the region of highly restrictive governments.
How does VPN work?
To understand the working structure of a VPN facility, we need to assess both scenarios-
When we access a website without a VPN, The ISP helps us to connect to that particular website. ISP gives us a unique IP address but since it’s the ISP only who is handling and directing all our traffic, it can definitely find out about the data that are being processed which makes it obvious that our privacy is being compromised.
When we connect to the internet with a VPN, the VPN application on our device which is also known as VPN Client establishes a secure connection with the VPN server. Our traffic still passes through the ISP but this time ISP will not be able to figure out the final destination of our data. The website we are visiting will also not be able to see our original IP address.
Types of VPN:
There are two basic types of VPN:
Remote access VPN:
- Through Remote access VPN, users can connect to other networks via a private encryption tunnel. It can connect them to the company’s internet server or public network.
- This VPN enables the client to associate with a private network and access all of its resources and services remotely.
- It is useful for both businesses and individual users. Users who are mindful of Internet security prefer using such VPN services to upgrade their internet privacy and security.
- Corporate employees can use this VPN to access their company’s network while working from home or any remote location.
Site-to-Site VPN:
It is also known as Router-to-Router VPN which is most popularly used in corporate environments, especially when any enterprise has its branches across the globe at multiple locations. In this situation, a site-to-site VPN creates a closed internal network as such that facilitates all the locations to work and coordinate together. Site-to-Site VPN can be categorized as follows-
Intranet-based VPN-
When workplaces of a similar organization are connected using a Router-to-Router VPN where the network access is granted to the personnel of that organization only.
Extranet based VPN-
When multiple organizations create a closed internet connection using site-to-site VPN where a branch of one organization establishes contact with the workplace of another organization.
In a site-to-site VPN, one point works as a VPN client, and another point as a VPN server as it depends on the Router-to-Router correspondence. When the verification is approved between the two points, only then the correspondence begins.
Types of VPN protocols:
There are many ways in which packages are sent and data exchange is performed over the internet. As a delivery partner customize the packaging of your product according to the nature of the item to be delivered, VPN protocols also determine how your data is sent over a VPN network.
A VPN protocol is a set of rules on how the data will be packaged and sent over a private network through established VPN tunnels to safely exchange data. VPN allows you to connect to a remote server as if you are connected with a wire, making a separate and distinguished network for outsiders. To make this sort of connection possible, we need VPN tunneling protocols to establish a safe tunnel for your data to reach the remote server and bypass firewall restrictions. Each VPN protocol has particular traits that make them better at some specific tasks.
Let us explore the types of VPN protocols that are most commonly used:
Internet Protocol Security (IPSec)
- It secures Internet Protocol communications (IP network). IPSec is often paired with other VPN protocols like L2TP to provide encryption, but it can also be used by itself. It’s frequently used for site-to-site VPNs.
- It verifies the session and encrypts each data packet during a session.
- IPSec runs in two modes: Transport mode and Tunneling mode.
- The information that you send using Transport mode, is divided into small chunks called Data Packets. The message in the data packet is encrypted using Transport Mode.
- In Tunneling mode, these small data packets are combined and the whole data packet is encrypted, which forms a tunnel-like structure.
Layer to Tunnelling Protocol (L2TP):
- It is a tunneling protocol that is often combined with another VPN security protocol like IPSec to provide a high level of secured connection.
- L2TP was developed by Cisco and Microsoft in the 90’s.
- L2TP generates a tunnel between two L2TP connection points i.e. the sender and the receiver.
- It provides a decent speed but not as fast as PPTP.
Point to Point Tunnelling Protocol (PPTP):
- PPTP is generally used when one organization wants to send data to another organization. It generates a tunnel and encrypts each of the data packets.
- It is one of the most widely used VPN protocols and has been in use since the early version of Windows OS got released. It was originally developed by Microsoft for Dial-up networks.
- It can also be used on Mac OS and Linux Operating Systems apart from Windows. It is compatible with most of the Operating Systems and that is what makes it one of the most prominent protocols.
- Due to the lower encryption standard, PPTP is one of the fastest VPN protocols. But when it comes to security, the encryption facility that it provides cannot be trusted as compared to other protocols.
SSL and TLS Protocols (Secure Socket Layer and Transport Security):
- These protocols come into account when the client is using a web browser to communicate with the server to access some particular services. It generates a VPN connection where the web browser acts as a client.
- User access is prohibited to specific applications instead of the entire network, therefore a user can only use a limited segment of the network via this protocol.
- These protocols are generally used by online shopping websites as they involve personal and sensitive data of the customer like Banking details, address, mobile number, order tracking details, etc. SSL and TSL protocols cannot be used for all sorts of data and are only used for sensitive data because of their high cost.
- In SSL connections, the URL starts with ‘HTTPS’ instead of ‘HTTP’ where ’s’ stands for secure.
Open VPN:
- It can be figured out by the name itself that this is an Open Source VPN that can be generated as per the client’s requirement. Clients can modify the level of security as per their usage. It is one of the newer protocols which was initially released in 2001.
- Open VPN is always a solid option, especially when the setup is handled by a third-party application.
- It is used for creating Point-to-Point and Site-to-Site connections.
- It uses a traditional security protocol based on SSL and TLS.
- It is the default protocol used by most the paid VPN providers. It supports several encryption algorithms, the most common being AES and Blowfish.
IKEv2 (Internet Key Exchange version 2):
- It is not exactly a VPN protocol but can be assumed to be useful. It was jointly developed by Microsoft and CISCO.
- It’s especially useful for mobile devices on 3G or 4G LTE because it’s good at reconnecting whenever the connection drops out. This can happen when the user drives through a tunnel and temporarily loses service or when they switch from mobile connection to wifi.
- It can establish connections much faster as compared to Open-source VPN.
- IKEv2 is not widely supported, but for those devices that are compatible, it’s quite easy to set up.
Secure Shell:
It can provide several options for strong authentication and protect communication security and integrity with strong encryption.
WireGuard:
- WireGuard is a security-focused virtual private network (VPN) known for its simplicity and ease of use. It uses proven cryptography protocols and algorithms to protect data.
- It was originally developed for the Linux kernel but is now available for Windows, macOS, BSD, iOS, and Android.
- It is the newest and enhanced version of the VPN Tunnel protocol that aims to achieve better speed, ease of deployment, and overhead.
- It uses a concept called “crypto key routing” to handle network management and access control in place of complicated firewall rules.
- However, Wireguard assigns IP addresses statically and not dynamically, which means some user data needs to be stored on the server.
Limitations of VPN:
Though VPN provides several benefits like hiding your browsing history, IP address, location, streaming location, devices, and web activity, it has certain disadvantages also. Comparatively slow speed, No cookies protection, and lack of total privacy can be some of them. The security provided through VPN is undoubtedly striking but still, it cannot be considered as a 100% secured connection as it might safeguard your data from external hackers, ISPs, and government but your details still can be seen by your VPN provider. Therefore, it is highly recommended to avail of VPN services from a trusted VPN provider only.
While selecting a suitable VPN provider, you must focus on certain points:
- It should offer sufficient speed.
- Your privacy should be kept secure.
- The provider should be using the latest protocol.
- The reputation of the provider should be good.
- The data limits provided should match your requirements.
- You should also know about the location of the server.
- It should offer VPN access on multiple devices.
- The cost of a VPN should be suitable.
- The highest encryption should be made available and the best customer support should be there.
- Free trials and ad blocking facilities should be provided.
VPN facility can be availed on each device that has an active internet connection including your laptops, tablet, smartphones, voice assistants, smart appliances, and smart TVs as well. Several VPN providers provide trial versions of their services with certain data usage limitations. You can download VPN clients for multiple devices from the site of these providers along with the free trial versions. Some of the best VPN providers of 2021 that are recommended are as follows:
VPN is a very beneficial facility that should be utilized for good. It’s in our hands whether we use it for achieving something positive or to accomplish malicious motives. Select sincerely and use wisely.





Looking for even stronger privacy protection? Utopia P2P goes above and beyond by offering an integrated web proxy functionality. Now you can level up your online security without needing to purchase costly VPNs or proxies separately. Start browsing safely with Utopia P2P today.