How to Avoid Hackers and Cheaters in PUBG Mobile
Most of you love playing PUBG Mobile. Many of you opt this game as … Read more

What’s at Play with Smart TOYS? Hidden Risks for your Child…
For children raised with technology, smart toys are just the new normal. More and … Read more

Top 10 technologies that could be exploited or hacked in the coming decade
The coming decade will see massive breakthroughs in the domain of technology, and I, … Read more

How a USB condom can make it safe to charge smartphones anywhere?
Details about Data Protector USB (Condom) – Protect your Smartphone Data and sensitive info … Read more
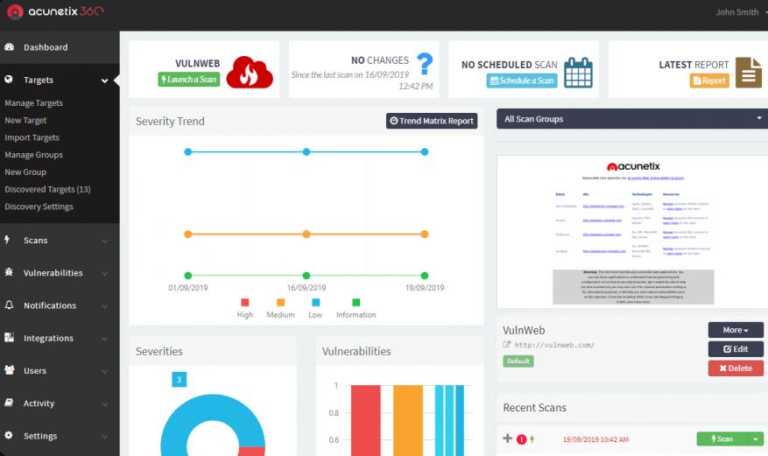
Top 8 Ethical Hacking or testings Tools for White hat Hackers
We know the term Hacking and usually, it is done by hackers to harm … Read more
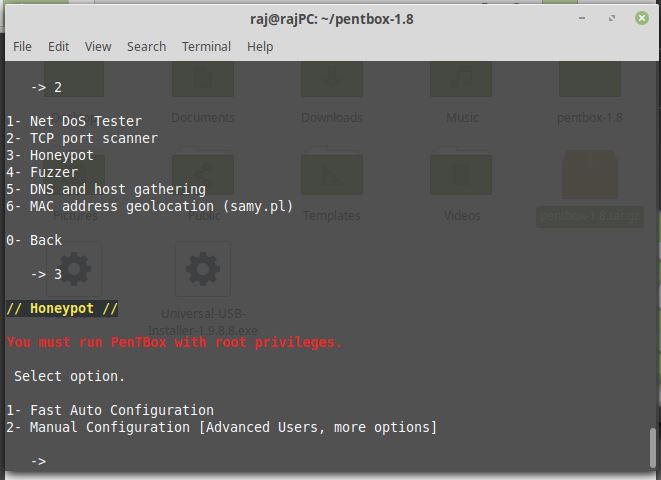
How to install Honeypot trap on Kali Linux to detect intrusion
If you are a new student of White Hat hacking or Ethical Hacking course … Read more

‘Juice Jacking’ Cybercriminals Use Public USB Ports to Steal Personal Data
Travellers have been advised by the Los Angeles District Attorney’s Office to avoid free … Read more

The Growth Hacking Book Launched for Start-ups and Entrepreneurs
Press Release: “The Growth Hacking Book: Most Guarded Growth Marketing Secrets the Silicon Valley … Read more
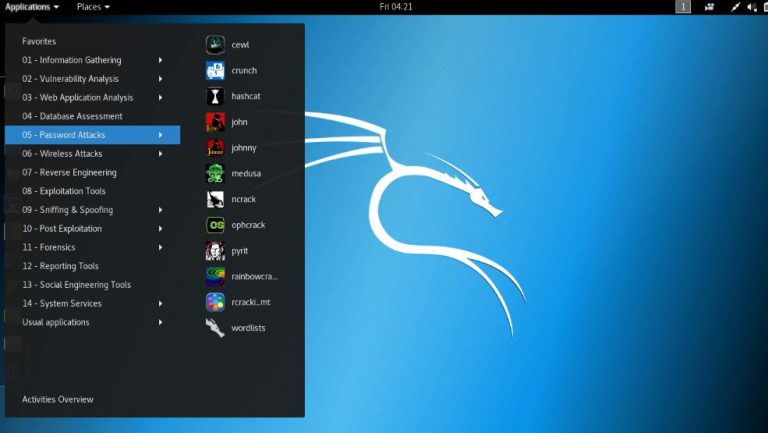
9 List of Best Free Penetration Testing tools
Things you need to know about Pentesting: Penetration Testing or often called PenTesting tools are … Read more

Marriott International hotel database hacked, 500 million customer data leaked
According to the Reuters, Marriott International said that its Starwood hotels room reservation database … Read more

BlackBerry new encryption technology can prevent hacking by quantum computer
As the terminal business becomes bleaker after the corresponding business is transferred to TCL … Read more

iPhone hacking software is being sold for $50 million
A well-known iPhone hacking software cum malware, Pegasus, was illegally tried to sold third … Read more

How to secure your WordPress Blog or Website from Hackers
The internet is flooded with nasty professional hackers and plagiarizers. They can harm a … Read more